How Security Architects Fit Into OrganizationsHow Security Architects Fit Into Organizations
Describing a security architect to the uninitiated is a tricky task, especially given the variable nature of the role. Here, we explain what security architects do and to whom they typically report.

How do you explain what security architects do and to whom they report -- and why? It is a tricky question. Some security architects work for a CTO office, others for cyber defense service delivery teams or CISO organizations. Plus, both software vendors and consultancies employ them. They all help improve a company’s security posture, just in different ways.
What Security Architects Do
The term “IT architect” refers to specialists who design and implement solutions, plan complex IT infrastructures and enterprise application estates, manage their lifecycles, or act as senior technical specialists and advisors (Figure 1). The most visible are software or application architects. They mastermind the design, implementation, parameterization, and configuration of concrete software products, including the integration with other solutions.
In traditional custom software development, software architects transform user requirements to a Java or Dotnet design, which five or fifty developers implement. Custom software, however, is a niche topic in security. Standard software dominates. As a result, companies need application architects who understand concrete security solutions such as Azure Information Protection or Broadcom DLP. They provide technical and product guidance for setting them up, configuring them to meet company-specific requirements, and integrating them with other applications such as log or incident management solutions.

Figure 1 - A typology for security architects
Enterprise or domain architects work on the big picture rather than a single application. Their typical tasks are:
Identifying and prioritizing capabilities. Data loss prevention, data governance, and malware scanning on Mac laptops -- which technical capabilities does an organization need, and what are the implementation priorities?
Mapping capabilities to applications. Which application is responsible for protecting high-privileged users? Azure PIM or an external solution such as CyberArk? Do we use the same tools for the cloud and the on-premises data center?
Managing the technology lifecycle: Software vendors phase out products, innovative new players challenge the status quo, and pricing models change -- today’s perfect application landscape might be in ruins a few months later. Security architects answer questions such as whether to replace Broadcom DLP with Microsoft Defender, understand the cost impact of changes, and identify at least the most significant milestones of such transformations.
Enterprise security architect or security domain architect are both titles for experts working on these topics. The exact titles can highlight whether the focus is more on strategy or tangible tasks, but these are nuances. In practice, the factual company context determines the daily work more than the job titles.
Finally, architect can be a job title reflecting and expressing an employee’s experience. Many companies offer functional careers (i.e., career paths beyond people and project management). Examples are highly skilled cryptography experts, IAM engineers who understand a specific technology and the company landscape in every detail, or experts who can “get solutions to work” in complex and challenging company environments. Security architecture job titles are ways to promote them without forcing respected engineers to manage teams.
Ultimately, the company size determines the level of differentiation and sophistication of the security architecture roles. A smaller SME might have one security architect, larger ones a dedicated domain or enterprise architect, plus application architects for IAM, network, and one for all other security tools. Global enterprises have dedicated security architecture teams, plus dozens of application architects masterminding specific products.
Functional Areas in Security Architecture
The best-known security architecture domains are identity and access management and network security. The latter works on zoning and firewall topics (i.e., how to structure a network to hinder lateral movements while allowing components and applications to interact). Identity and access management covers authentication and authorization for internal employees, but nowadays also for customers, partners, and suppliers interacting with company services and applications. Active directory, LDAP, and identity provider are technologies and buzzwords in this area.
The expansion and growth of CISO organizations drive their need for tool support to ensure efficiency, especially for logging network and IAM events, identifying potential attacks, and security incident management. Splunk, Sentinel, Microsoft Defender, and Jira are typical solutions for turning log events into actionable items and managing potential security incidents. Architects help with the initial design and maintain and evolve such solutions over the years.
Finally, there is a growing number of dedicated security services and applications such as data loss prevention, data classification, sandboxes for malware analysis, malware scanning, and vulnerability scanning. They all require clever minds to make them work and deliver value to an organization.
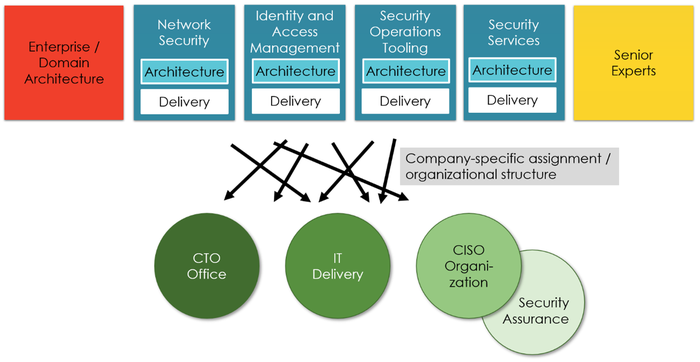
Figure 2 - Architectural roles, delivery teams, and teams with security architects
Teams in Which Security Architects Work
CTO offices, security service delivery teams, CISO organizations, and vendor or consulting companies all need security architects. Security software vendors send product experts to their customers to help them implement and optimize their installations. Consulting companies need experts to help their clients address technology-specific or technology-strategy-related challenges. But which security architects work in a CTO office, a delivery team, or a CISO organization? The shaping of security teams and CISO organizations decides. It is not so much to whom a CISO reports but more on its tasks and responsibilities.
The easiest to understand is the placement of software and application architects. They are typically working as part of security application and service delivery teams. These delivery teams are potentially part of the CISO organization or form a dedicated cyber defense unit in a larger organization. Domain and enterprise security architects can be part of the CTO or the CISO organization. It is a company-specific organizational choice.
One category of security architects can be found (hopefully) in any CISO organization: senior technical experts helping analyze incidents, supporting security assurance, writing guidelines, and consulting for complex security topics. The more technically demanding the tasks of a CISO organization get, the higher the need for such experts.
Security architects are crucial for designing and guiding implementations of an organization’s security posture. When applying for a security architecture position or hiring a candidate understanding the nuances is vital for the perfect match -- and crucial for everyone and every organization dedicated to fighting all evil in cyberspace.
About the Author
You May Also Like









