Quantum Computing Could Make Today's Encryption ObsoleteQuantum Computing Could Make Today's Encryption Obsolete
July 18, 2017
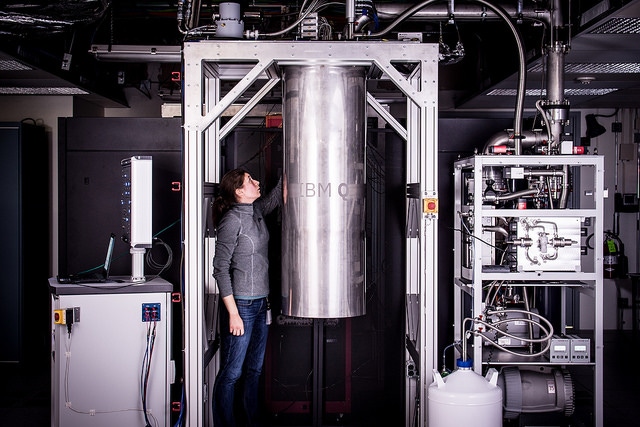
This is the first post in our new regular series on data center security. Scroll to the bottom of the article to learn more about the column and its author.
Researchers at top university and corporate labs around the world are in a furious race to create the first practical, usable quantum computer. Quantum computers — which use quantum bits, or qubits — are capable of running computations impossible for existing technology. It promises to open up new possibilities in areas like medical research, artificial intelligence, and security.
Oh, and they would also easily crack current encryption algorithms.
How close are quantum computers to becoming reality? The point at which quantum computers would surpass our current computers in capability is at about 50 cubits.
In March, IBM announced that it had a 20-qubit quantum computer, and that outside researchers and developers could already start running simulations on the IBM Quantum Experience.
In June, Google raised the ante. Alan Ho, an engineer from Google’s quantum AI lab, told a conference in Germany that Google already had a 20-qubit system, and was planning to built a 49-qubit computer by the end of the year.
See also: Google’s Quantum Computing Push Opens New Front in Cloud Battle
“Quantum computers are now commercially available if you have a lot of money,” said Mike Stute, chief scientist at Masergy, a networking, security and cloud communications technology company headquartered in Plano, Texas.
The problem is that dealing with qubits requires some tricky engineering involving quantum physics. Plus, quantum computers require built-in error correction to deal with the fact that qubits are not as well-behaved as the traditional zero-or-one bits of classical computing. These two challenges combine to make the development of larger quantum computer a difficult task.
Meanwhile, it’s not enough to just surpass current computers. In order to crack today’s encryption, quantum computers have to be a lot better than what we have today.
That will take between 500 and 2,000 qubits, said Kevin Curran, a senior member at IEEE and cybersecurity professor at Ulster University.
See also: One Click and Voilà, Your Entire Data Center is Encrypted
So, run-of-the-mill hackers won’t be breaking into banking systems right away. Government agencies, however, may have quantum computing technology a generation or two ahead of what’s commercially available, said Masergy’s Stute.
That means companies protecting data of interest to China, Russia, or the NSA might need to be particularly careful.
What You Can Do
Current encryption is based on the idea that there are some mathematical problems that are really hard for computers to solve.
For example, public-key encryption — where one key is used to encrypt the data, and a different key to unlock it — typically relies on just those kinds of problems.
“When quantum computing becomes a reality, then many public-key algorithms will be obsolete,” said Curran.
Symmetric encryption, where the same key is used to both encrypt and decrypt the data, is more robust and will last longer.
Companies that have data they want to protect may want to start planning ahead to make more use of symmetric encryption, as well as switch to longer keys.
In addition, researchers are already working on new, quantum-proof encryption methods and will start testing them as soon as quantum computers become more widely available.
For companies that depend on having good encryption in place the most important thing is not to hard-wire encryption systems into their applications.
Instead, they need to adopt a modular approach, so that they can easily replace old, obsolete algorithms with new, effective ones. With some advanced planning, that’s not hard to do.
Introducing Our New Data Center Security Column
Cyberattacks with wide-reaching consequences are now commonplace. Last month’s attack on FedEx’s TNT Express will hurt its quarterly results. The same month, thousands of members of the British Parliament and their staff lost access to email as a precautionary measure taken to limit the damage from a massive cyberattack on the legislative body. If your job has anything to do with your organization’s data centers, cybersecurity is becoming a bigger and bigger part of it, which is why we’re introducing a new column focused exclusively on data center security.
It’s a great pleasure to introduce Maria Korolov, who will author the column. She is a Massachusetts-based technology journalist who writes about cybersecurity and virtual reality.
During her 20 years of experience covering financial technology and cybersecurity she wrote for Computerworld, was a columnist for Securities Industry News, ran a business news bureau in China, and founded a publication covering virtual reality. She has reported for the Chicago Tribune, Reuters, UPI, and the Associated Press.
Before switching to business and technology journalism, she was a war correspondent in the republics of the former Soviet Union and has reported from Chechnya, Afghanistan, and other war zones.
About the Author
You May Also Like







